
Cyber Security – will we ever be ready?
Do you feel protected against cyber intrusions?
- With the increase of companies moving their delicate information and operations to the cloud, is this not a motivator for hackers?
- Is being told that your intellectual property is protected, believable?
One would argue that it is the small companies that are prone to risk, however of late, the news has been reporting about organisations you would typically never think could be infiltrated.
So, is having a large budget in Cyber Security really that important?
The more you hear about companies being affected by intrusions – it makes you question are we ever fully protected?
I had the pleasure of reading an article by Andy Bochman, Internet Security. He shares a lot about the controversy of this belief of being “Protected”
Andy Bochman mentions something that I find quite interesting, “Identify the functions whose failure would jeopardize your business, isolate them from the internet to the greatest extent possible, reduce their reliance on digital technologies to an absolute minimum, and backstop their monitoring and control with analog devices and trusted human beings.”
This comment makes complete sense and I see how it could help protect a company, however, with the increase in remote offices, flexible working locations, offshore managed services etc, this approach isn't always a feasible option. Ensuring remote access to necessary services while maintaining the necessary levels of infiltration protection, is something Security experts are continually experimenting with.
Some key points to note in the meantime to help minimise your current risks:
- Implement a Two Factor Authentication or Multi Factor Authentication
- Continual re-evaluation, communication of processes and policies
- Continual education for staff around email security, downloads, links, passwords, what to share and what not
- Written and verbal confirmations, physical sign offs and incorporating more than one signature
- Test your staff and re-educate
It is always good to know what threats are out there:
- APT (Advanced Persistent Threat)
- Phishing
- Ransomware
- DDoS (Distributed Denial of Service)
- BEC (Business Email Compromise)
- Web Application Attack
Gain an understanding of what the threats are and investigate the best way to safeguard yourself against them.
A useful guide which I learned about from attending a BNZ and Telstra Cyber Security Discussion, was the below diagram. The five knows of cyber security - More details about this can be found here - Telstra.
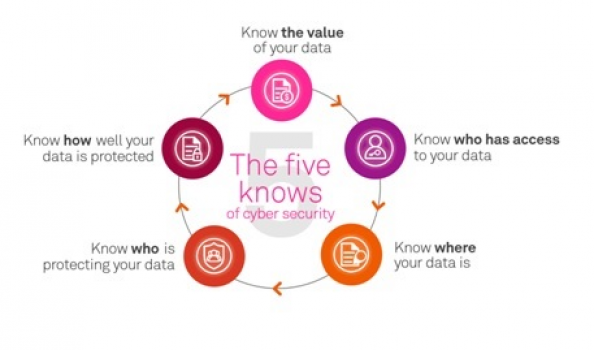
If you as an organisation cannot answer any of these five questions, I would recommend you have a discussion and consider seeking the consultation of someone who can give you advice on your cyber security.
At Alpha Recruitment we specialise in the contract and permanent placements of Cyber Security Consultants.
I recently voiced this question to Telstra Chief Information Security Officer - Berin Lautenbach and Head of Information and Cyber Security - Martyn Bayly at an event.
"Where do they see the future of Cyber Security, because it always seems to be a tug of war, the smarter the systems become the smarter the infiltrators become?"
They shared a valid point in reply and said in order to progress, for us to move forward we can’t let the “infiltrators” hamper progress. We need to move forward and continue on this path. We can minimise the impacts and mitigate some risks, but as long as we keep moving forward.
I thought about this comment immensely and have concluded that in order for human kind to keep progressing to the next level in technology and business, there is going to be casualties and mistakes.
There will be those who will try to prevent and harm this progression, but as long as we keep moving forward for the greater good, as with any technological breakthrough from the past – we will get there.
The risks are there but during this journey, this IT evolution, there is going to be moments which take us two steps back but as long as we take five steps forward afterwards, we’ll be OK.
Article from our Senior IT Consultant - Christopher Kourie
